Configure AWS Credentials
How to configure your AWS credentials for programmatic access
- how to configure your AWS credentials for programmatic access
- how to deploy Webiny in a more controlled and secure manner using our Deploy Webiny Project AWS CloudFormation template
This article guides you through configuring your AWS credentials for programmatic access. At the end of the tutorial, you will have your API keys and region configured to successfully deploy Webiny to your AWS cloud.
If you prefer the video version, check out our YouTube video below:
Step 1: Create Your AWS Account
In that case skip to step 2 to create your programmatic user.
To create your AWS account and set up your IAM credentials we should first navigate to the AWS Console page 
 aws-sign-in
aws-sign-inNext click on Create a new AWS account:
 aws-login
aws-loginNow input your credentials and create your account:
 aws-register
aws-registerStep 2: Create a User for Programmatic Access
Once you’re registered, login and head to the AWS Management Console and select IAM under Security, Identity & Compliance:
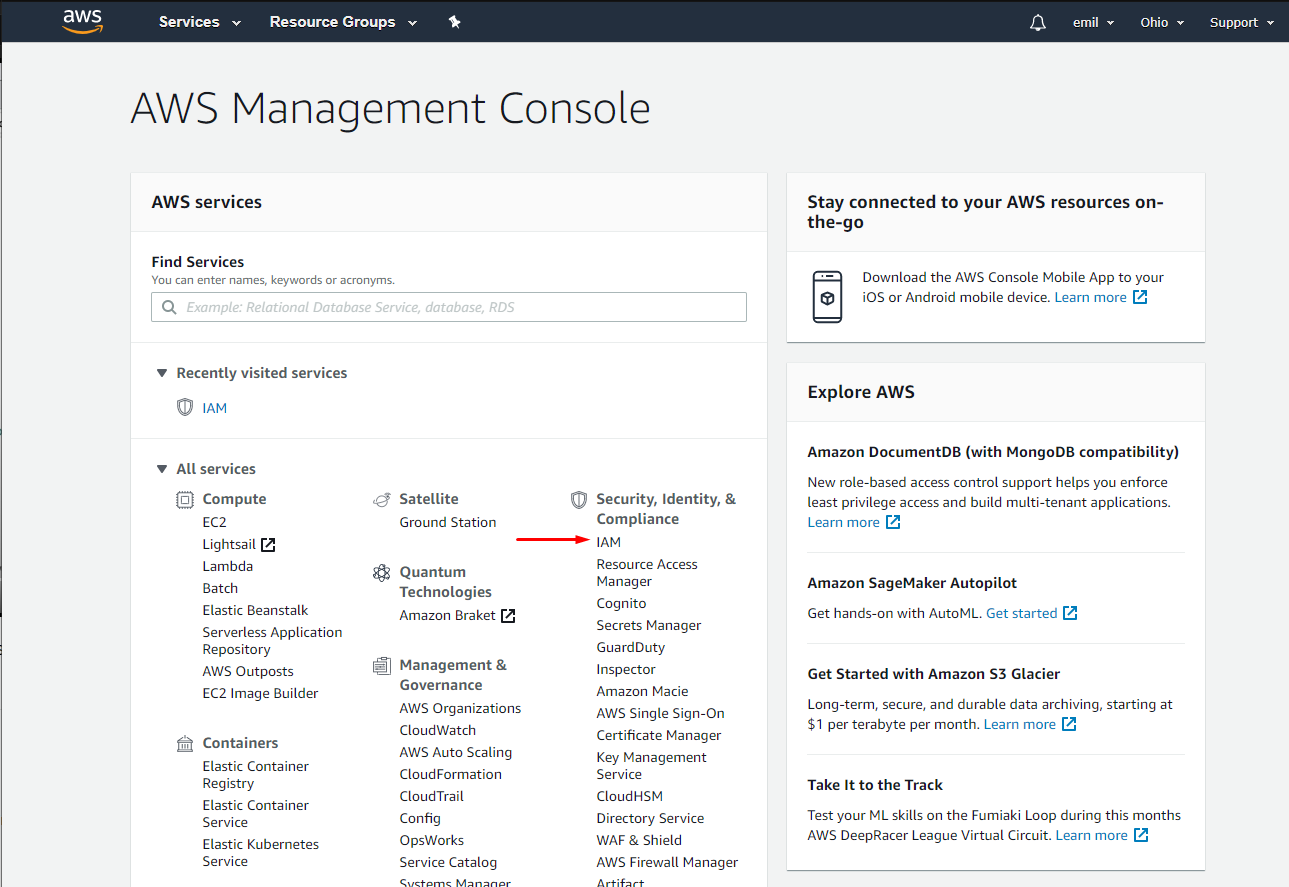 aws-iam-selection
aws-iam-selectionClick on IAM and select Users under Access Management:
 aws-iam-users
aws-iam-usersClick on Add user to create the account with the IAM credentials:
 aws-create-user
aws-create-userHere you enter a 5-step process, and the first step is to create a User name for the credentials.
Make sure to select the Programmatic access checkbox before moving to the next step.
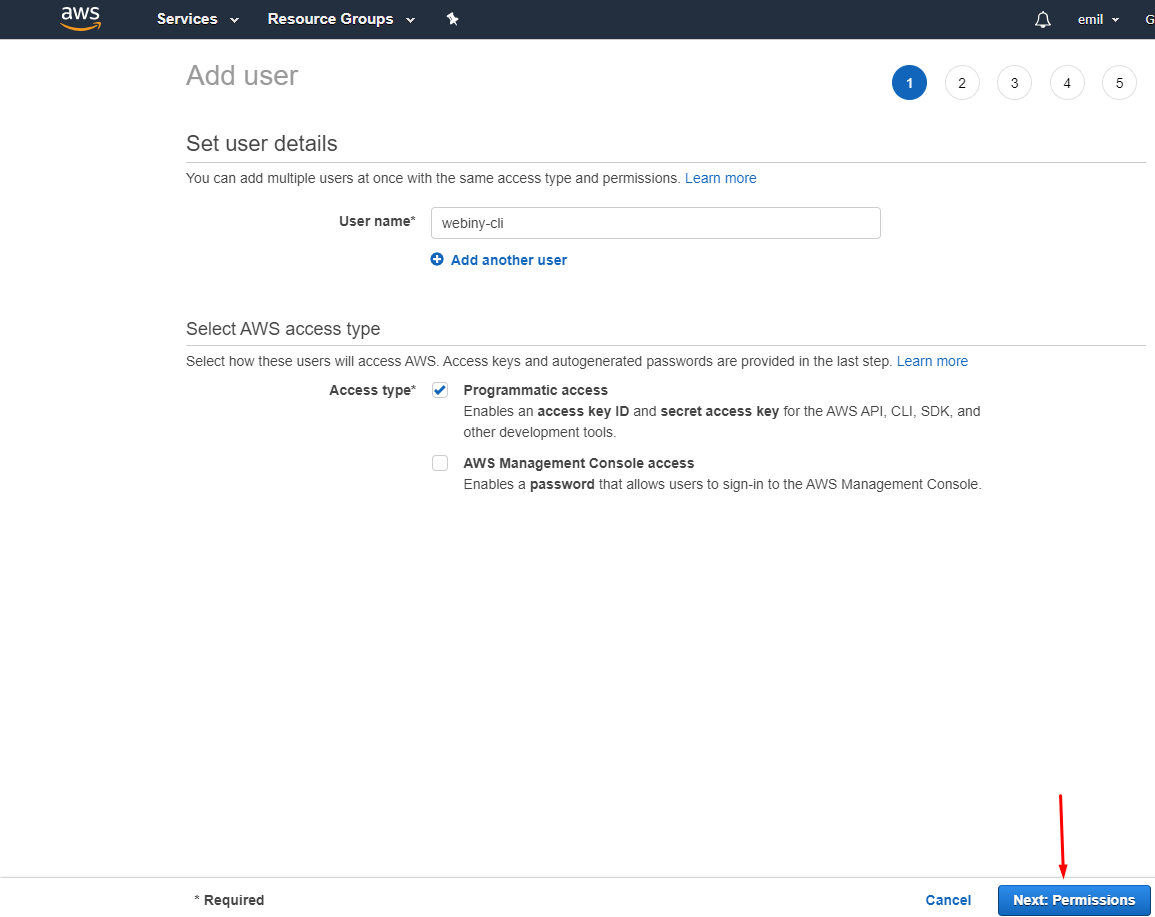 aws-user-details
aws-user-detailsIn the next step you define the access level for the new user. Select Attach existing Policies from the three options that are available. Then select the AdministratorAccess policy by marking the checkbox next to it. When ready, click the Next:Tags button:
In case your organization cannot use the AdministratorAccess policy or you need to have a more strictly defined set of permissions,
please see the “Deploy Webiny Project” AWS CloudFormation Template section.
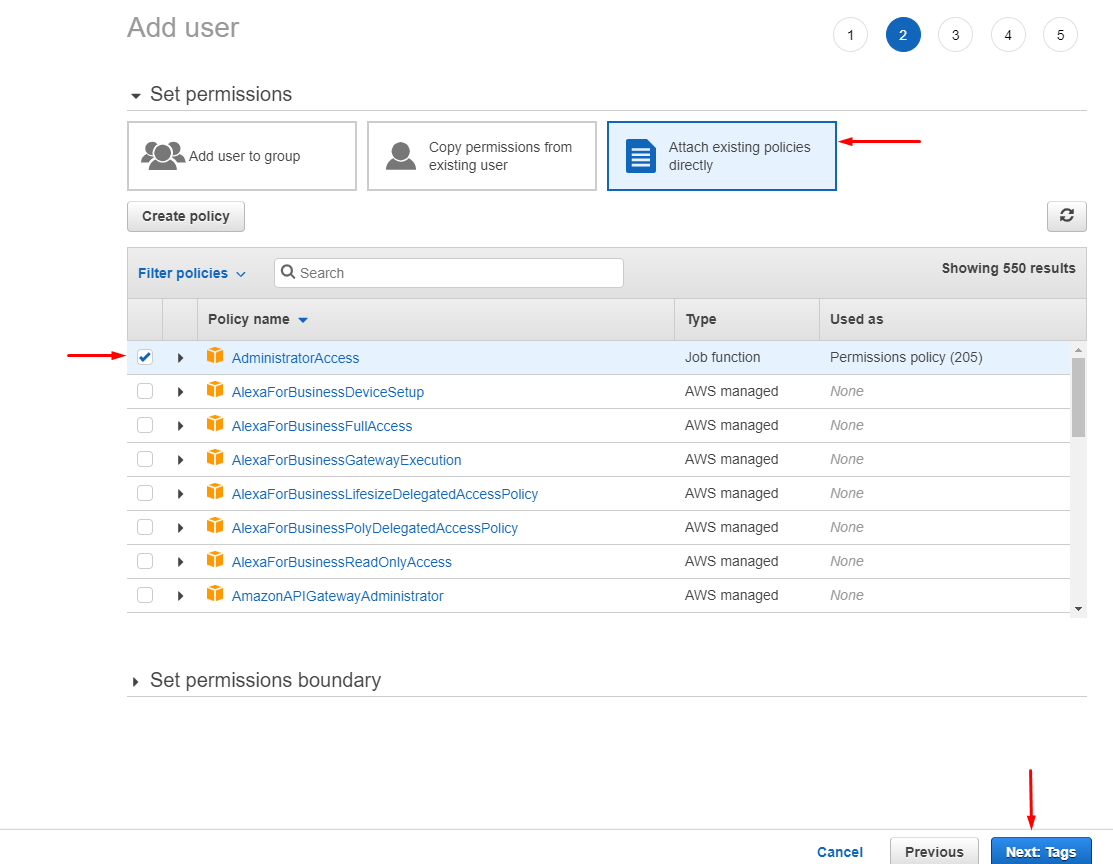 aws-user-permissions
aws-user-permissionsIn case you don’t want to add any tags to your new user, you can just skip this step and click the Next:Review button.
 aws-user-tags
aws-user-tagsAfter all the steps are complete, you’ll see a Review page. It should look something similar to this. If everything is correct, click the Create user button.
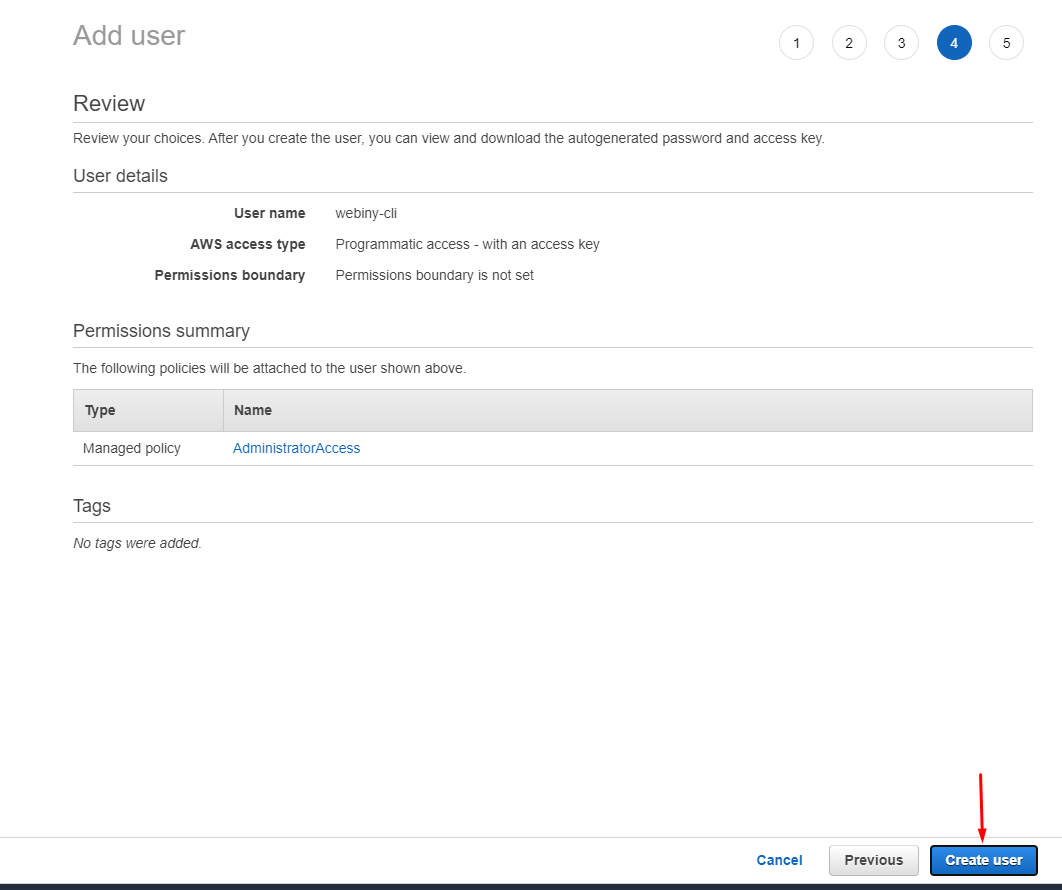 aws-user-review
aws-user-reviewLastly, you will receive a success message with your Access key ID and Secret access key. You need to copy these strings and keep them safe as you need them for the next step.
Once you navigate off this screen, you will not be able to see the credentials any more. If you lose them, you will need to delete the user and create a new one.
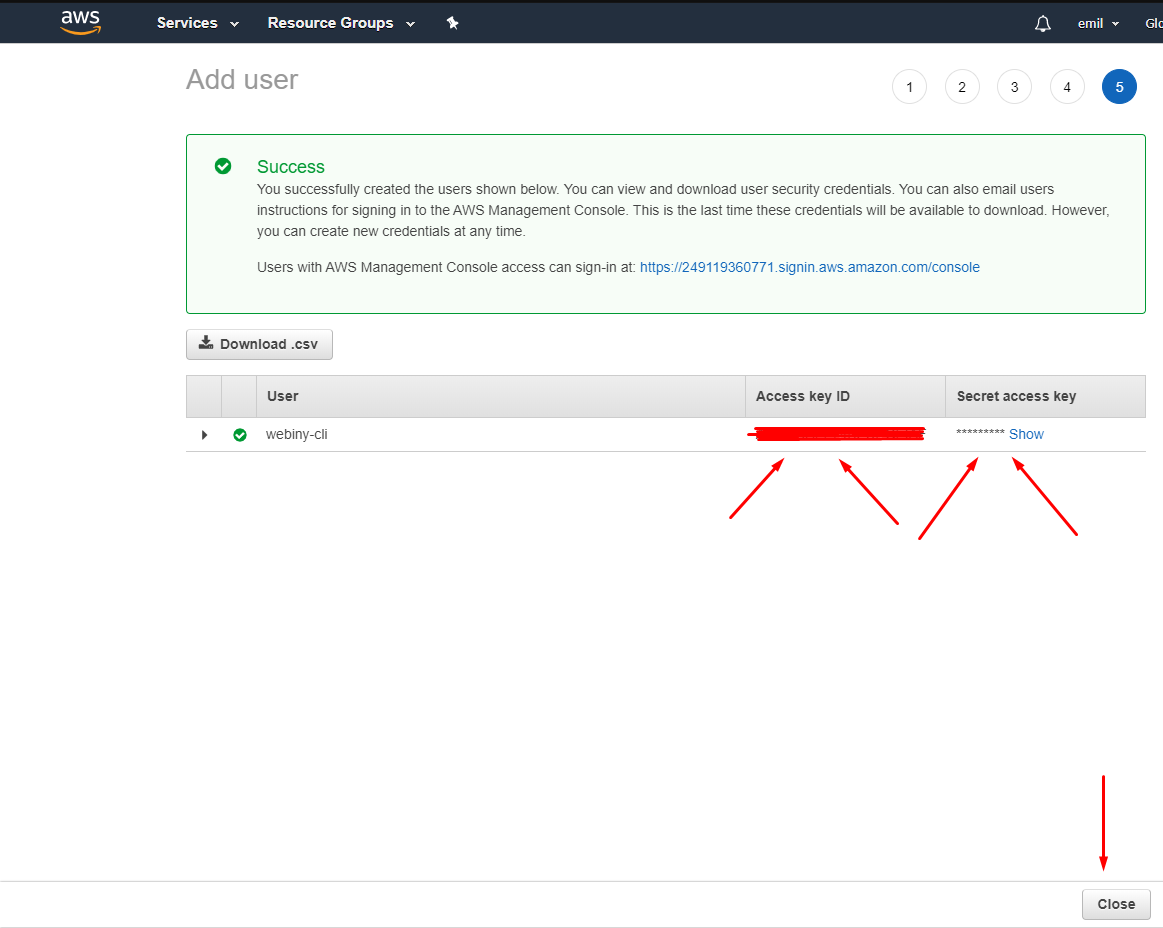 aws-user-created
aws-user-created"Deploy Webiny Project" AWS CloudFormation Template
In order to deploy your Webiny project in a more controlled and secure manner, you can utilize our Deploy Webiny Project AWS CloudFormation template. Via three IAM user groups, the template deploys necessary (least-privilege 
To get started, simply click here 
 .
.Step 3: Configure the Programmatic Access
Now that you have the Access key ID and Secret access key it’s time to store them on your development machine.
Unix Setup
If you’re on UNIX, create a folder named .aws inside your user folder, that’s ~/.aws. Inside that folder place a file called credentials. So the full path is ~/.aws/credentials.
Windows Setup
On Windows machines, navigate to your user folder. That’s C:\Users\USERNAME\ (replace USERNAME with your actual username). Inside create a new folder named .aws, and inside the .aws folder create a file named credentials. The full path should be like this: C:\Users\USERNAME\.aws\credentials.
Now that we have our credentials file, edit the file and populate it like so:
[default]
aws_access_key_id = PASTE_ACCESS_KEY_ID_HERE
aws_secret_access_key = PASTE_SECRET_ACCESS_KEY_HEREThe word default inside the square brackets is your profile name. If you don’t explicitly configure a profile name, the default profile is used by AWS CLI and SDK.
And that’s it! You now have your AWS credentials, your default region, and you’re ready to deploy Webiny.
FAQ
Is There a Way to Check if My Profile Was Set Properly?
If you have the AWS CLI 
aws sts get-caller-identity
This should give an output similar to the following:
{
"Account": "x",
"UserId": "y",
"Arn": "arn:aws:iam::x:user/z"
}